Let’s be real: Homebrew is amazing. It’s the missing package manager for macOS that every developer loves. However, in an enterprise environment, Homebrew can also be a security nightmare waiting to happen. World-writable binaries? Third-party taps from who-knows-where? Supply chain attacks through git remote hijacking? Yeah, that’s exactly what keeps security teams up at night. […]

How to Update Your Apple Account When Your Organization Reclaims the Domain
Your Work Email Can’t Be Your Apple Account Anymore: Here’s What to Do A step-by-step guide to updating your Apple Account when your organization reclaims their domain So you just got an email from Apple telling you to change your Apple ID email address, and you’re wondering if it’s a scam.. It’s not. Your organization […]

Don’t Let Personal Apple Accounts Hijack Your Domain: The Complete Guide to Apple Business Manager Domain Capture
A deep dive into domain lock, domain capture, and managed Apple accounts for IT administrators Picture this: you’re the IT administrator for a large organization, and you’ve just discovered that over 5.000 employees have created personal Apple Accounts (Apple IDs) using their work email addresses. Their vacation photos, music libraries, health data, and app purchases […]
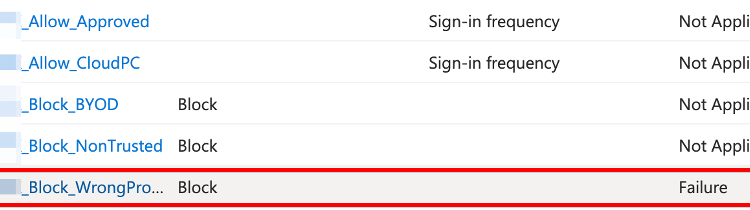
A Deep Dive into Location and Device-Based Access Control
“Because sometimes your security requirements make you question your life choices” 🤠 A Word of Warning Before We Start Conditional access policies and Device-Based Access Control are fun and all, however, let me be crystal clear before we dive into this: I do not advise excluding users from MFA. In fact, I think it’s… well, […]
Tracking Microsoft Defender PUA Policy Changes with Intune Custom Attributes
In the ever-evolving battleground of endpoint security, Microsoft Defender for Endpoint stands as a vigilant guardian against the rising tide of cyber threats. But even the best guardians can sometimes be a bit… forgetful. What happens when your Microsoft Defender PUA Policy settings start changing mysteriously on your macOS devices? In my previous post we […]

How I Accidentally Fort Knox’d myself: A macOS Security Hardening Tale
The Road to Better Security Is Paved with Infinite Login Loops If you’re reading this, you probably care about macOS security hardening. And like me, you might be interested in hardening your macOS devices according to industry standards. But let me tell you a cautionary tale about implementing security measures without proper testing, or as […]
Advanced macOS Protection with Microsoft Intune – Beyond the Basics
Advanced macOS Protection with Microsoft Intune: The Security Sequel You Didn’t Know You Needed!🚀 Hey there, security enthusiasts and Mac wranglers! Remember when we thought CIS Level 1 was the cool kid on the block? Well, grab your Terminal windows and hold onto your MDM profiles, because Level 2 is here to rock your config. […]

Book Review: Mastering Windows 365
Mastering Windows 365 by Christiaan Brinkhoff, Sandeep Patnaik, and Morten Pedholt Introduction After days of exploring Mastering Windows 365, I can confidently say this book offers more than technical guidance alone. It’s a complete roadmap to mastering Windows 365. Christiaan Brinkhoff, Sandeep Patnaik, and Morten Pedholt deliver practical knowledge, real-world experience, and step-by-step strategies that […]
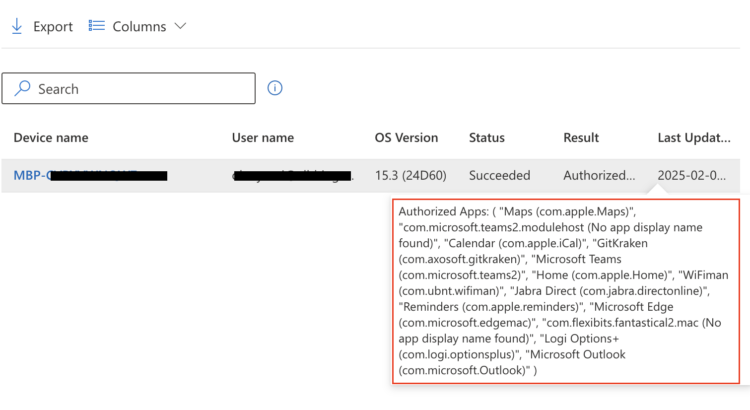
Who’s Watching? Auditing macOS Location Services with Intune.
In my ongoing mission to strengthen macOS device security with Microsoft Intune, today I’m focusing on macOS Location Services, and 2 recommendations from the CIS Level 2 benchmarks for macOS devices. We’ll explore recommendation 2.6.1.2 Ensure ‘Show Location Icon in Control Center when System Services Request Your Location’ Is Enabled and recommendation 2.6.1.3 Audit Location […]
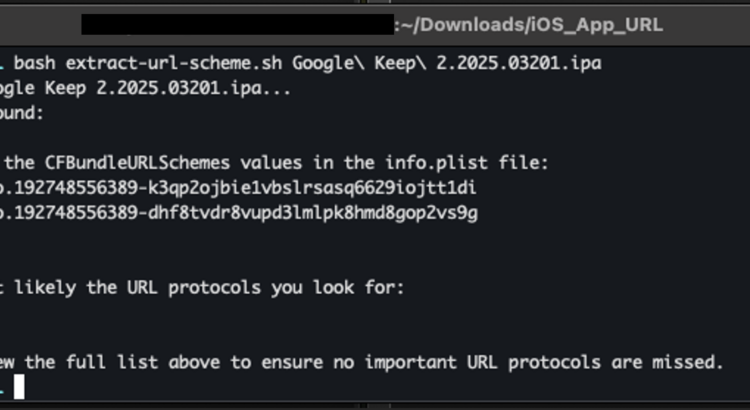
iOS MAM Policies; Discovering URL Protocols and Data Transfer Exceptions
It’s been a while since I did a blog on Mobile Application Management (MAM) policies, the unsung heroes of modern IT security. They quietly ensure that corporate data stays safe, even on personal devices. However, when it comes to data transfer exceptions, those tricky settings that allow unmanaged apps to interact with managed app data, […]
